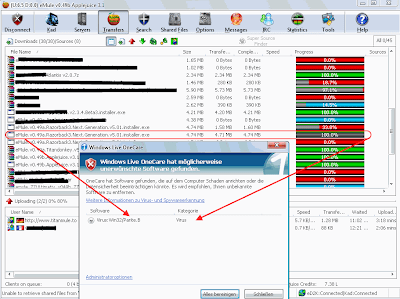
Recently found in some eMule.v0.49a.Razorback3.Next.Generation.v5.01.installer.exe
its original done with NSIS installer Virus Win32/Parite.B, Age/Date: 27. May 2008
eMule.v0.49a.Razorback3.Next.Generation.v5.01.installer.exe witch is clean have file hash:
MD5: 2a2f735b5f78eed8bf6ab1feec58bd20
SHA1: b91fcba385e679e41f26d004170729bd8a5cb49a
This Virus can be possible not found with some AV Scanners if it is a changed variant from the old Virus Win32 Parite b, year 2003 - 2004 Viruslist.com - Virus.Win32.Parite.b.
Todays updates from Live OnCare Microsoft AV can remove and eliminate it.
You can try latest Norman Malware Cleaner Build 2008.08.07: http://download.norman.no/public/Norman_Malware_Cleaner.exe
Or
MS Live OnCare online scanner:
http://onecare.live.com/site/en-us/scanner/install.htm?scanner=default
Tested Scanner that can't detect it:
Avast Pro 4.8 080811-0 FAILED
Rising 20.57.11 FAILED
McAfee Security Suite
...many more...
Use no installer packs, use bin zip, rar, etc... if the software is available as no setup version like here: or extract installer using universal extractor (Homepage) to take only the content from installers/Setups.
Read more:
http://board.raidrush.ws/archive/t-373517.html
http://forum.hijackthis.de/showthread.php?t=3982
http://www.bitdefender.de/site/Search/?query=parite
older: http://www.trojaner-board.de/30926-win32-parite-b-nicht-runterzubekommen.html
http://forum.avast.com/index.php?topic=37344.0
http://www.eset.com/threat-center/pedia/virusy/win/win32/pariteb.htm
5 comments:
Just downloaded from them homepage. Same MD5
Please submit to Kaspersky if it's different as this:
Type: Win32 polymorphic fileinfector virus
Affects: Windows 95, Windows 98, Windows ME, Windows NT, Windows 2000, Windows XP
Upon infection the virus adds a new section (this section is randomly named with 3 letters followed by the ASC-II character 07) to the host file, which contains the main viral code in encrypted form. This file is later dropped as a randomly named temp-file into the TEMP folder using windows API function to retrieve this path.
The temp-file (around 172Kb in size) is injected into Windows Explorer. This means that if Explorer runs, the virus stays active in memory.
The virus takes the Original Entry Point (OEP) from the infected file out of the Fileheader, encrypts the old Entry Point with a randomly generated 32bit value, and stores this calculated entrypoint value in the encrypted last section of the file, where the virus writes itself.
It needs the original entry point to execute an infected file after the viral code has been executed - otherwise infected programs would not be able to run after the virus runs.
Note: In the following text, %windir% denotes Windows directory (e.g. C:\WINDOWS) and %system% denotes Windows System directory (e.g. C:\WINDOWS\SYSTEM32) as they differ on various versions of Microsoft Windows.
The virus creates the following Registry key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\PINF
Parite uses 2 different, randomly generated, 32bit values, at 2 random addresses in the original host file, and it overwrites these addresses if the file does not run.
If the infected file is active, the virus restores this data out of the encrypted section into the program code. This is a special mechanism to make the cleaning of infected files more difficult.
The virus enumerates and scans all network shares and tries to infect all Windows32 executables and screensaver files.
Other Details
The polymorphic Dropper is written using TASM, and the virus part itself is written with Borland C++ and packed with UPX, a executable file compressor.
Makes computer run slow?
Troj:
212.227.109.0 - 212.227.109.255
kundenserver.de
in Firewall
Schlund + Partner AG
nice proxy there:
http://www.Google.pl/search?q=xaze.xs4all.nl
Post a Comment